
- What is ransomware?
- How does ransomware spread?
- How does ransomware get on my devices? – 5 Steps
- What to do if I have ransomware?
- Should I pay the ransom?
- Ransomware survival guide checklist
- 2020 Ransomware facts
- How to prevent ransomware
- The most popular types of ransomware
- Examples of ransomware screenshots
- Ransomware on Android
- Ransomware myths
- Top 2020 ransomware news stories
- How to detect ransomware
- Ransomware FAQ
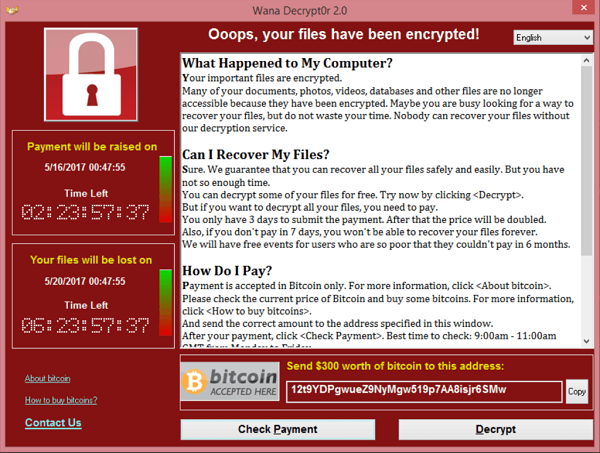
Ransomware: Malicious software that encrypts your data, blocking access to your computer with a splash-screen of instructions until a sum of money is paid. The preferred method of payment is through an untraceable virtual currency called bitcoin. Victims are alerted that unless a sum of money is paid within a time frame, their files will be destroyed. Here’s an example screenshot of ransomware:
The 5 Steps in a Typical Ransomware Attack
Infection – Step 1 You may have opened an email attachment or clicked on a link in an unsolicited email such as a phishing email. Or you may have an infected application. Besides email, ransomware creators can also infect you by using exploit kits. You may have visited an infected website that’s able to exploit your browser and other software that’s running on your device. Finally, RDP – known as remote desktop connection. Port-scanners scour the internet looking for open RDP ports. The ransomware installs itself on the endpoint and any network it can access. Secure Key Exchange – Step 2 The ransomware on your network contacts the cybercriminals, alerting them a successful exploit is underway. The request for decryption keys are made and generated. Encryption – Step 3 The ransomware starts using military grade encryption algorithm. There’s AES, RSA, and ECDH encryption. (Some ransomware variants use a hybrid of encryption methods). Encrypting files on the victim’s device is in progress. The victims computer may slow down. Encryption will occur on any files on the local device and the network. Extortion – Step 4 A splash screen appears to the victim with instructions. Every type of ransomware has a uniquely designed splash screen with a unique deadline of payment. All ransomware threatens to destroy one’s data if the specified payment is not made. Payments are usually demanded in the form of a bitcoin payment because they’re untraceable. Figuring out how to purchase a bitcoin and setting up a wallet can be another pain. Unlocking – Step 5 Victims can either pay the ransom in exchange for the decryption keys (no guarantee the cyber criminal will pay) or attempt to start their disaster recovery process. This process will remove the ransomware and restore the network from clean backups.
These facts about ransomware ignite many business owners to take immediate action in ransomware prevention:
– A new organization will become a victim of ransomware every 14 seconds in 2019, and every 11 seconds by 2021. – Ransomware attacks double in 2019, brute-force attempts increase – Ransomware was the #1 type of malware of 2018 and has no sign of slowing this year in 2020. – 75% of companies infected with ransomware had up-to-date endpoint protection. – Only having a proactive disaster recovery plan in place will increase your chances of surviving a ransomware attack. – 50% of a surveyed IT security professionals claim there are connected devices accessing their networks that they’re unaware of. – Only 1 in 3 said devices purchased by their organization are cleared by security personnel. – Data loss and downtime are still the biggest consequences of ransomware. – It’s important for businesses to know their vulnerabilities and take preventative matters into their own hands.
Follow these steps:
Our most important tip is hiring a trusted managed IT service provider such as hyphenet to do all the prevention for you and to ensure it’s being properly done. (it’s a LOT of work keeping your network safe – we can make it easy for you) #1 Updates Keep all your browsers, operating systems, and software up-to-date and patched. When hackers learn about a new patch or security update, they will seek out vulnerable businesses for an easy pay day. Don’t install software that you’re unfamiliar with and do not grant it administrative privileges. Do install whitelisting software that prevents unauthorized software from and applications from executing. Update to Windows 10! Update your operating system to Windows 10. It makes ransomware prevention easier by preventing unauthorized apps from accessing your Windows system files and personal data. However, you need to make sure your windows 10 has this security setting turned on! (it’s not on by default!) It’s called Controlled Folder Access. Here’s the steps how to turn on the new anti-ransomware features in the Windows 10 Fall creators Update: First, we’ll make sure you’re using the Fall Creators Update – version 1709: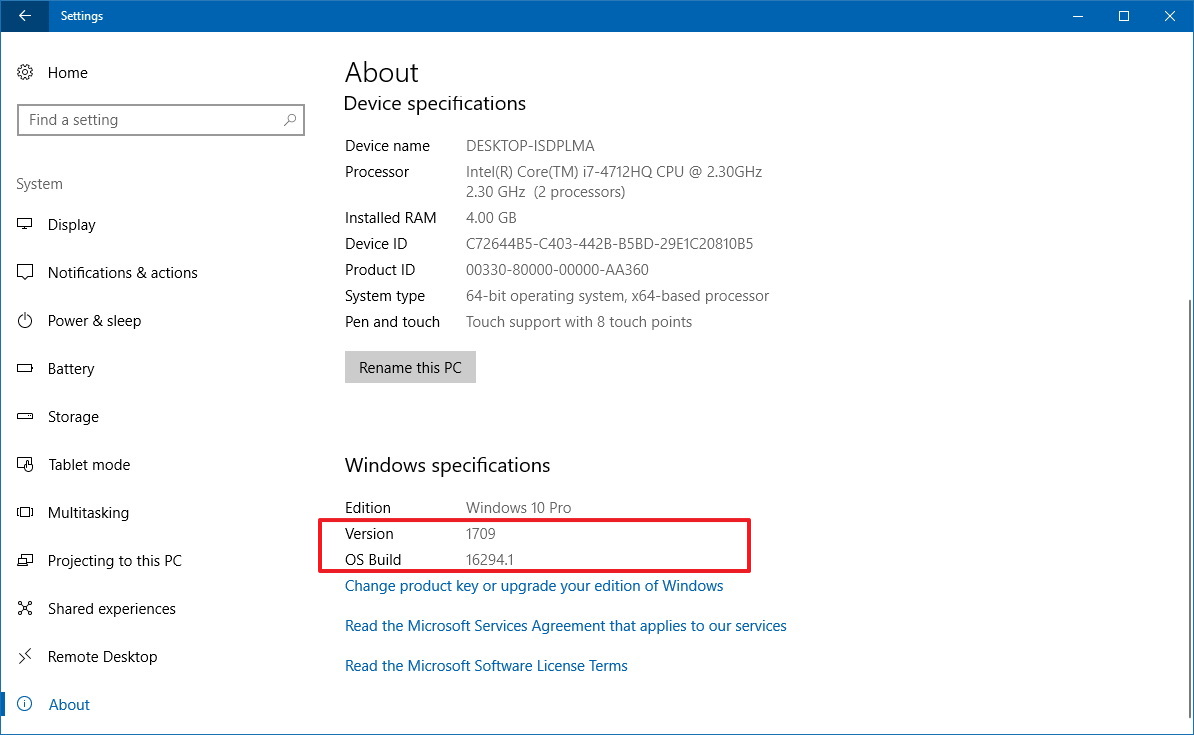 Open Settings > System > About. There you’ll see a list of details, look for Version: 1709
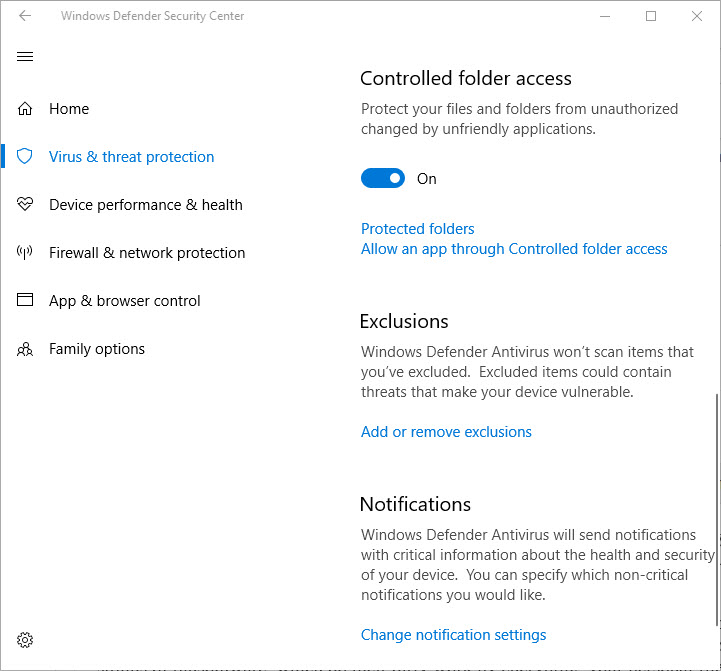
Next, open the Windows Defender Security Center. Virus & threat protection > Virus & threat protection settings and turn on the switch under Controlled folder access:
Open Settings > System > About. There you’ll see a list of details, look for Version: 1709
Next, open the Windows Defender Security Center. Virus & threat protection > Virus & threat protection settings and turn on the switch under Controlled folder access:
 You can take your security even further. Change the default settings using these advanced these steps:
Double check your Protected Folders:
Click Protected folders to identify which folders are currently being protected from malware and suspicious apps.
Double check your whitelisted apps:
Click Allow an app through controlled folder access to view and select your whitelisted apps. Allow your most used and trusted apps that you know are safe.
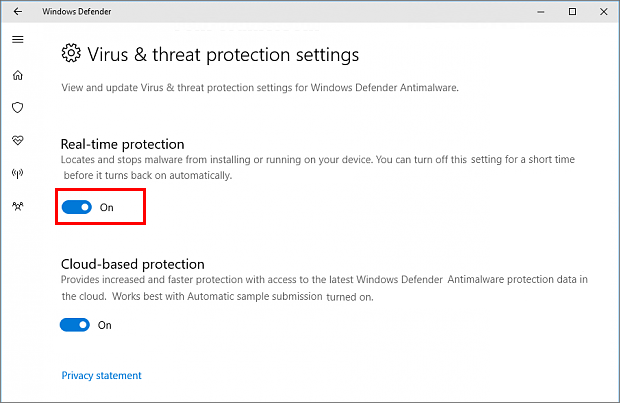
Please note: You must have Windows Defender real-time protection enabled. Here’s how to turn it on below:
Go to Settings app > click Update & Security > select the Security tab > Select: Choose the antivirus program you want to use. Windows Defender Antivirus will automatically turn on.
You can take your security even further. Change the default settings using these advanced these steps:
Double check your Protected Folders:
Click Protected folders to identify which folders are currently being protected from malware and suspicious apps.
Double check your whitelisted apps:
Click Allow an app through controlled folder access to view and select your whitelisted apps. Allow your most used and trusted apps that you know are safe.
Please note: You must have Windows Defender real-time protection enabled. Here’s how to turn it on below:
Go to Settings app > click Update & Security > select the Security tab > Select: Choose the antivirus program you want to use. Windows Defender Antivirus will automatically turn on.
 Running Windows 10 for Enterprise?
You’ll have to uninstall all your current antivirus programs first.
Note: This feature does not work with third-party antivirus software.
#2 Educate Employees
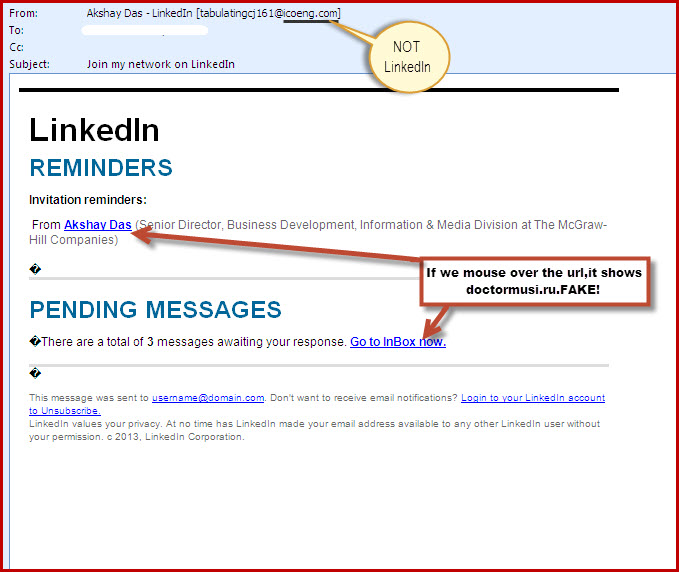
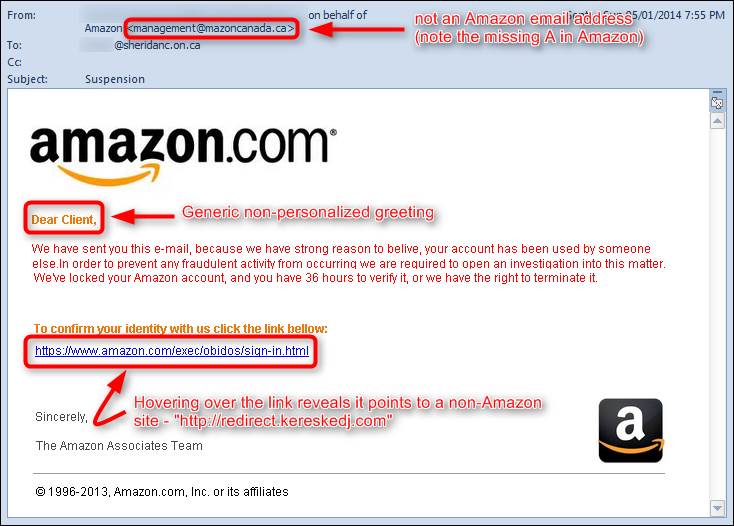
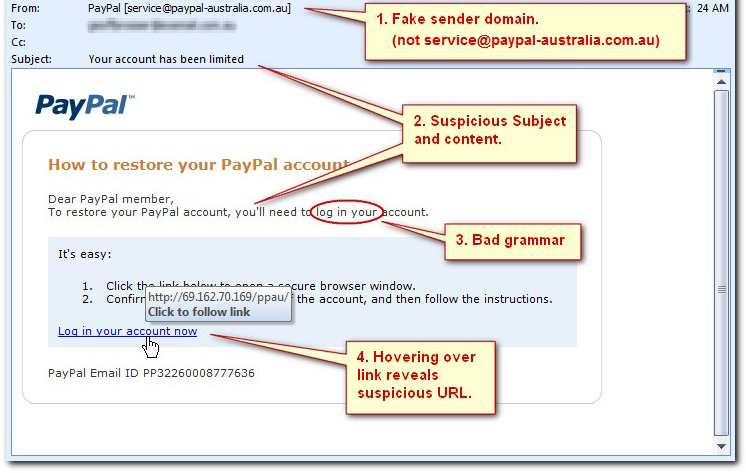
Your employees are one of your biggest vulnerabilities. They could become targets of social engineering, spear phishing, etc. One wrong click on a spam email could bring an IT disaster such as ransomware.
FREE Resource:
FREE Cyber Security Training + Quiz for your Employees
Educate your employees about:
– Social engineering
– How to detect suspicious emails
– Scams
– Suspicious websites
– RDP Remote Desktop Connection
– Enable the “Show file extensions” option in the Window settings
– Stay away from extensions such as “.exe, .vbs, .scr”
– Disconnecting the PC immediately from the network and Wi-Fi if unusual activity occurs
– Think before clicking
– Enforce Strong Password Security – Password management
#3 Add Layers of Security
Think your anti-virus software is enough to keep out cyber criminals? Unfortunately, now we need specialized layers of security to protect, detect, and block ransomware attacks before they happen. Consulting with an IT company can also help you find your network’s vulnerabilities and strengthen them. You need to know your unique networks vulnerabilities and protect them.
We offer a FREE onsite Network Security Scan + Report.
Schedule a FREE on-site visit today!
For the most secure protection:
– Firewall
– Antivirus with Active Monitoring
– Anti-Malware
– Anti-Ransomware
– Anti-exploit
– Hosted Anti-spam : Add Virus control at the Email Server Level
– Block incoming mail with executable attachments
– Protect your RDP access (Remote Desktop Protocol)
– Change the RDP port (mentioned below)
– Block Vulnerable Plug-ins: Such as Java and Flash
– Limit Internet Connectivity – Keeping internet away from critical servers can help combat ransomware
– Setup Viewable File Extensions – Help prevent you from clicking on a .exe executable file (.exe, vbs, or .scr)
Call us for all the right security protection for your business:
(619) 325-0990
Change the RDP port so port-scanners looking for open ports will not find yours! Instructions on tunecomp.net
What’s RDP? Remote desktop protocol allows remote control of a PC.
If a hacker finds your default RDP port (port 3389 by default) they can start a brute force attack on your login/password prompt.
Finally, Make a stronger password for your RDP
How to protect your RDP access from ransomware attacks – malwarebytes
#4 Create Restore & Recovery Points
Using Windows? Setup is easy, go to:
the control panel > enter in “System Restore” into the search function > Turn on system protection and create regular restore points. Also create restore points.
#5 Create Secure Backups of your Data (both onsite and offsite)
If you do get hit with ransomware and your data becomes encrypted, you will have these backups in place to restore your computer.
Backup data checklist:
– Backed up regularly
– Stored offsite (cloud)
– Backup devices such as external USB are disconnected
– Do not store files on the mapped drive
– Make sure you test your backups
The easiest and most effective data backup solution we recommend is Datto. Datto allows your to quickly restore (possibly in minutes) your network from any point of time aka using image based backups! You can empower your business and create Image Based Backups Today
We’re a datto partner and can provide you with the right datto backup for your organization and also a free quote. Get your datto pricing here.
Running Windows 10 for Enterprise?
You’ll have to uninstall all your current antivirus programs first.
Note: This feature does not work with third-party antivirus software.
#2 Educate Employees
Your employees are one of your biggest vulnerabilities. They could become targets of social engineering, spear phishing, etc. One wrong click on a spam email could bring an IT disaster such as ransomware.
FREE Resource:
FREE Cyber Security Training + Quiz for your Employees
Educate your employees about:
– Social engineering
– How to detect suspicious emails
– Scams
– Suspicious websites
– RDP Remote Desktop Connection
– Enable the “Show file extensions” option in the Window settings
– Stay away from extensions such as “.exe, .vbs, .scr”
– Disconnecting the PC immediately from the network and Wi-Fi if unusual activity occurs
– Think before clicking
– Enforce Strong Password Security – Password management
#3 Add Layers of Security
Think your anti-virus software is enough to keep out cyber criminals? Unfortunately, now we need specialized layers of security to protect, detect, and block ransomware attacks before they happen. Consulting with an IT company can also help you find your network’s vulnerabilities and strengthen them. You need to know your unique networks vulnerabilities and protect them.
We offer a FREE onsite Network Security Scan + Report.
Schedule a FREE on-site visit today!
For the most secure protection:
– Firewall
– Antivirus with Active Monitoring
– Anti-Malware
– Anti-Ransomware
– Anti-exploit
– Hosted Anti-spam : Add Virus control at the Email Server Level
– Block incoming mail with executable attachments
– Protect your RDP access (Remote Desktop Protocol)
– Change the RDP port (mentioned below)
– Block Vulnerable Plug-ins: Such as Java and Flash
– Limit Internet Connectivity – Keeping internet away from critical servers can help combat ransomware
– Setup Viewable File Extensions – Help prevent you from clicking on a .exe executable file (.exe, vbs, or .scr)
Call us for all the right security protection for your business:
(619) 325-0990
Change the RDP port so port-scanners looking for open ports will not find yours! Instructions on tunecomp.net
What’s RDP? Remote desktop protocol allows remote control of a PC.
If a hacker finds your default RDP port (port 3389 by default) they can start a brute force attack on your login/password prompt.
Finally, Make a stronger password for your RDP
How to protect your RDP access from ransomware attacks – malwarebytes
#4 Create Restore & Recovery Points
Using Windows? Setup is easy, go to:
the control panel > enter in “System Restore” into the search function > Turn on system protection and create regular restore points. Also create restore points.
#5 Create Secure Backups of your Data (both onsite and offsite)
If you do get hit with ransomware and your data becomes encrypted, you will have these backups in place to restore your computer.
Backup data checklist:
– Backed up regularly
– Stored offsite (cloud)
– Backup devices such as external USB are disconnected
– Do not store files on the mapped drive
– Make sure you test your backups
The easiest and most effective data backup solution we recommend is Datto. Datto allows your to quickly restore (possibly in minutes) your network from any point of time aka using image based backups! You can empower your business and create Image Based Backups Today
We’re a datto partner and can provide you with the right datto backup for your organization and also a free quote. Get your datto pricing here.

The common ransomware scenario. Is this you? You’re working on your computer it seems slower than usual; extremely slower.
Your computer’s chugging just to open a folder. Next, your computer is acting unusual. You’re unable to open documents. Now you’re receiving error messages for “Unknown file type.” Your work productivity has now come to a screeching halt. You’re locked out of your computer! There’s a bizarre error splash screen that looks something like this: Curious, you look around the office to see if anyone else is locked out of their computer. Hmmm… should I call the IT guy? Should I wait to see if it goes away?
YES! Call your Managed IT Service Provider because you’re infected with ransomware.
Alert them with the type of ransomware on the screen. You may want to take a photo of your screen to share with IT support. They will instruct you the proper actions to take depending on your network setup.
Understanding your options:
– Pay the ransom / Negotiate a price – No Guarantee
– Restore the files from a backup (make sure your backup is not encrypted – plug a drive into another PC) Fully wipe the drive and do a clean install of the OS and restore the files from a clean backup.
– See if there’s Decryption tools available.
– Remove the ransomware yourself using anti-virus or anti-malware software (see below)
– Reinstall from scratch – “Factory reset” on Windows 10 or use installation disks/ USB sticks.
– Call your Managed IT Service Provider to handle the situation
If you don’t have a Managed IT Service provider.
How to Handle Screen-Locking Ransomware Yourself:
#1 Disconnect your infected computer from the network – both wired and WiFi
Keep your data from leaking over the internet and stop the encryption of your files.
#2 Recover your data from backups
To ensure your computer is clean, you should recover your files from a previous backup on a separate drive. If you have a backup, you don’t have to worry about paying a ransom.
#3 Don’t have a backup?
You can give us a call (619) 325-0990 or try doing these steps yourself:
#4 Reboot your computer in Safe Mode.
(How to get into safe mode: Press the power button and the S key on the keyboard at the same time.)
* (if unable to get into safe mode see step #5.)
#5 Try a System Restore if Safe Mode does NOT work.
Most Windows PCs allow you to roll back to a last known good state.
Here’s how to do a System Restore:
–Windows 7: Restart your PC while constantly tapping the F8 key to get to the Advanced Book Options Menu. Choose > Repair Your Computer > Login with your password > and select System Restore.
–Windows 8, 8.1 or 10: Restart your PC while holding down the Shift key. This should prompt the recovery screen. Select Troubleshoot > System Restore.
#6 Still can’t reach the recovery screens?
Get your installation disk or USB disk for that version of Windows > Reboot from that and select > Repair Your Computer instead of installing the operating system.
#7 Run antivirus software to clean out your PC
NEED free antivirus?
Try downloading free virus scanners (because your anti-virus missed this ransomware virus) If you can’t download it from your computer, download it onto another computer and load it from a USB flash drive:
http://www.bitdefender.com/solutions/free.html
http://support.kaspersky.com/viruses/avptool2011?level=2
https://www.malwarebytes.org/
If using Malwarebytes, Run the quick scan. The scan can take anywhere from 5 to ten minutes.
If the scanner disappears, you have a deep infection that will kill any virus scanners. It’s best to call a professional with ransomware experience at this point or reinstall Windows / start from scratch.
If Malwarebytes detects infected files, click on Remove Selected button to start removing the infections.
When the Malware appears to be gone, restart your computer normally.
If the problem continues, repeat the steps and try the other malware scanners mentioned.
Once finished removing malware, make sure the home page is set to a safe site such as google.com. Many times, malware will set the homepage to a site that will reinfect your computer.
Start > control panel> internet options> home page settings.
We’re seeing an increase of ransomware victims, everyone from small businesses, large enterprises, schools, hospitals, PCs, mobile devices, you name it, it’s everywhere.
The sooner your take these actions, the less chance the infected computer can spread to other computers on the network and the less files the ransomware can encrypt.
#8 Report to the Authorities
The FBI urges all cases of ransomware attacks to be reported.
Here’s the link to report ransomware infections to the FBI
Our managed IT service provider will most likely have a clean backup to restore your files. Hopefully you’re paying them monthly for data backups – please double check your MSP agreement!
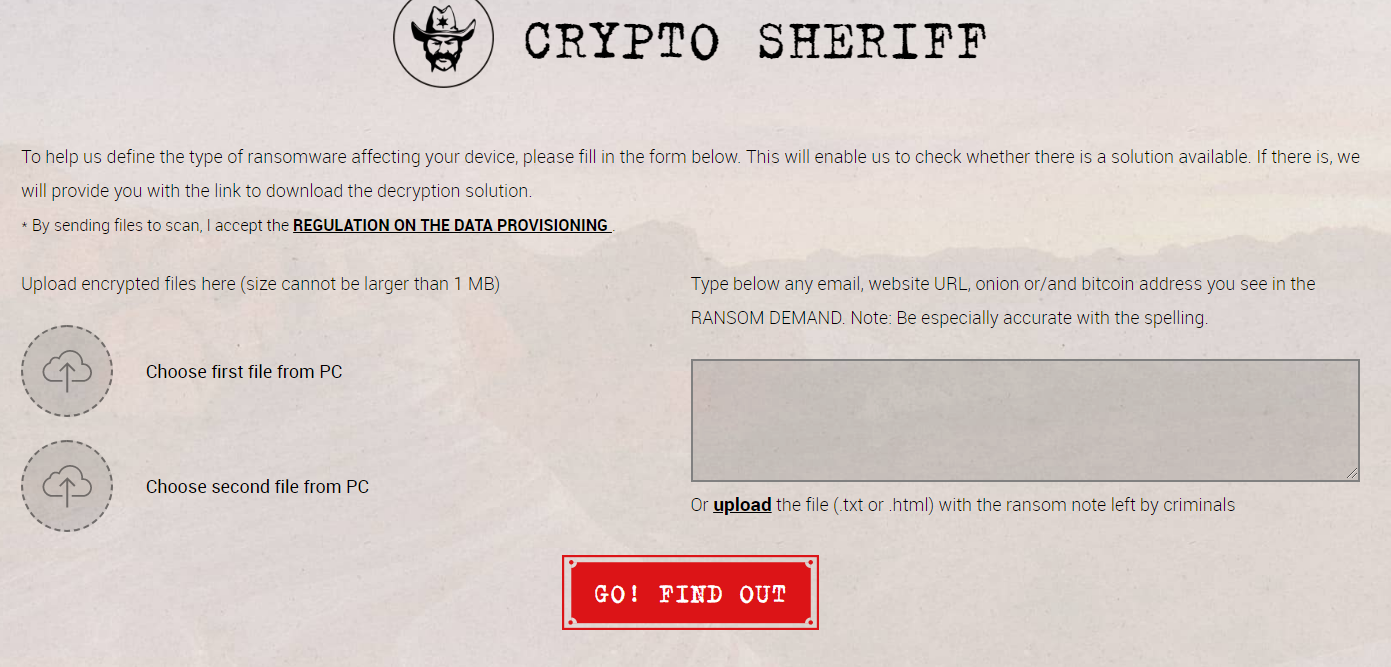
Sometimes there’s free decryption tools for known ransomware; free online. Check No More Ransom.org. No More Ransom – Crypto Sheriff – This free resource will help determine if there’s a free decryption key available!
Curious, you look around the office to see if anyone else is locked out of their computer. Hmmm… should I call the IT guy? Should I wait to see if it goes away?
YES! Call your Managed IT Service Provider because you’re infected with ransomware.
Alert them with the type of ransomware on the screen. You may want to take a photo of your screen to share with IT support. They will instruct you the proper actions to take depending on your network setup.
Understanding your options:
– Pay the ransom / Negotiate a price – No Guarantee
– Restore the files from a backup (make sure your backup is not encrypted – plug a drive into another PC) Fully wipe the drive and do a clean install of the OS and restore the files from a clean backup.
– See if there’s Decryption tools available.
– Remove the ransomware yourself using anti-virus or anti-malware software (see below)
– Reinstall from scratch – “Factory reset” on Windows 10 or use installation disks/ USB sticks.
– Call your Managed IT Service Provider to handle the situation
If you don’t have a Managed IT Service provider.
How to Handle Screen-Locking Ransomware Yourself:
#1 Disconnect your infected computer from the network – both wired and WiFi
Keep your data from leaking over the internet and stop the encryption of your files.
#2 Recover your data from backups
To ensure your computer is clean, you should recover your files from a previous backup on a separate drive. If you have a backup, you don’t have to worry about paying a ransom.
#3 Don’t have a backup?
You can give us a call (619) 325-0990 or try doing these steps yourself:
#4 Reboot your computer in Safe Mode.
(How to get into safe mode: Press the power button and the S key on the keyboard at the same time.)
* (if unable to get into safe mode see step #5.)
#5 Try a System Restore if Safe Mode does NOT work.
Most Windows PCs allow you to roll back to a last known good state.
Here’s how to do a System Restore:
–Windows 7: Restart your PC while constantly tapping the F8 key to get to the Advanced Book Options Menu. Choose > Repair Your Computer > Login with your password > and select System Restore.
–Windows 8, 8.1 or 10: Restart your PC while holding down the Shift key. This should prompt the recovery screen. Select Troubleshoot > System Restore.
#6 Still can’t reach the recovery screens?
Get your installation disk or USB disk for that version of Windows > Reboot from that and select > Repair Your Computer instead of installing the operating system.
#7 Run antivirus software to clean out your PC
NEED free antivirus?
Try downloading free virus scanners (because your anti-virus missed this ransomware virus) If you can’t download it from your computer, download it onto another computer and load it from a USB flash drive:
http://www.bitdefender.com/solutions/free.html
http://support.kaspersky.com/viruses/avptool2011?level=2
https://www.malwarebytes.org/
If using Malwarebytes, Run the quick scan. The scan can take anywhere from 5 to ten minutes.
If the scanner disappears, you have a deep infection that will kill any virus scanners. It’s best to call a professional with ransomware experience at this point or reinstall Windows / start from scratch.
If Malwarebytes detects infected files, click on Remove Selected button to start removing the infections.
When the Malware appears to be gone, restart your computer normally.
If the problem continues, repeat the steps and try the other malware scanners mentioned.
Once finished removing malware, make sure the home page is set to a safe site such as google.com. Many times, malware will set the homepage to a site that will reinfect your computer.
Start > control panel> internet options> home page settings.
We’re seeing an increase of ransomware victims, everyone from small businesses, large enterprises, schools, hospitals, PCs, mobile devices, you name it, it’s everywhere.
The sooner your take these actions, the less chance the infected computer can spread to other computers on the network and the less files the ransomware can encrypt.
#8 Report to the Authorities
The FBI urges all cases of ransomware attacks to be reported.
Here’s the link to report ransomware infections to the FBI
Our managed IT service provider will most likely have a clean backup to restore your files. Hopefully you’re paying them monthly for data backups – please double check your MSP agreement!
Sometimes there’s free decryption tools for known ransomware; free online. Check No More Ransom.org. No More Ransom – Crypto Sheriff – This free resource will help determine if there’s a free decryption key available!
NO!
Paying the ransom does not guarantee you will unlock your files. In addition to encrypting your data, the hackers may have also sold your data on the dark web. Paying will not take down the potential damage. There’s no incentive for the cyber criminal to send you the keys; once they have already been paid. Paying only encourages you to pay again. The servers used to receive payment are sometimes quickly taken offline. Sometimes it’s by law enforcement taking down the servers. Or it’s the cybercriminals, done to cover their tracks or move to their next ransomware campaign.
Hackers prefer bitcoin as payment because it’s fast, reliable, verifiable, and it’s easy to write software that can demand payment and and give notification when payment is received.

Yes. There are significantly less known cases of ransomware occurring on mac OS. However, not one has led to serious outbreaks.

Example 1:
 Example: 2
Example: 2
 Example 3:
Example 3:
WannaCry
WannaCry spread so rapidly worldwide in 2017! Affecting 116 countries. Easily the worst ransomware attack in history.
WannaCry Screenshot:
 Bad Rabbit
Screenshot of bad rabbit ransomware
Bad Rabbit
Screenshot of bad rabbit ransomware
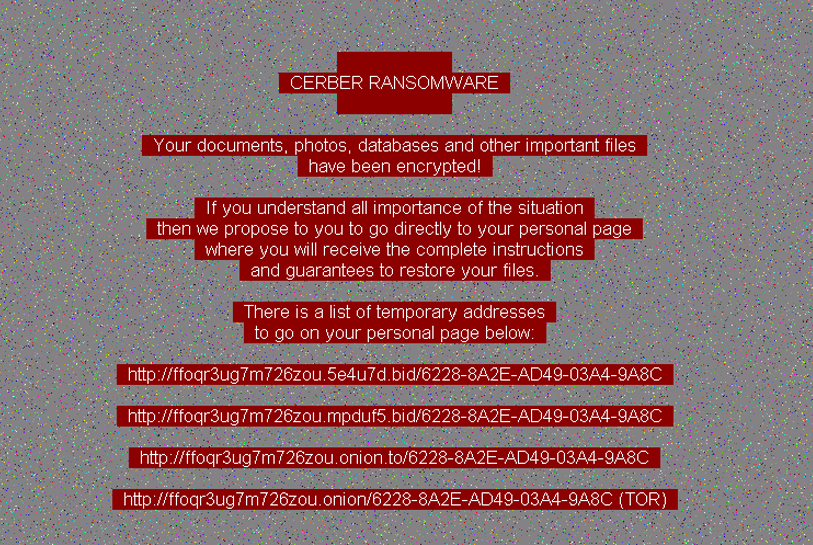
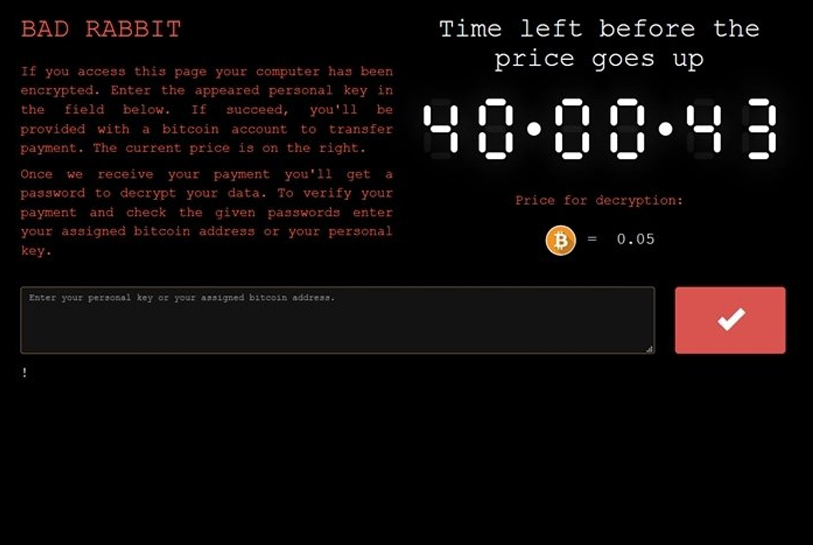 Cerber
Cerber screenshot:
Cerber
Cerber screenshot:
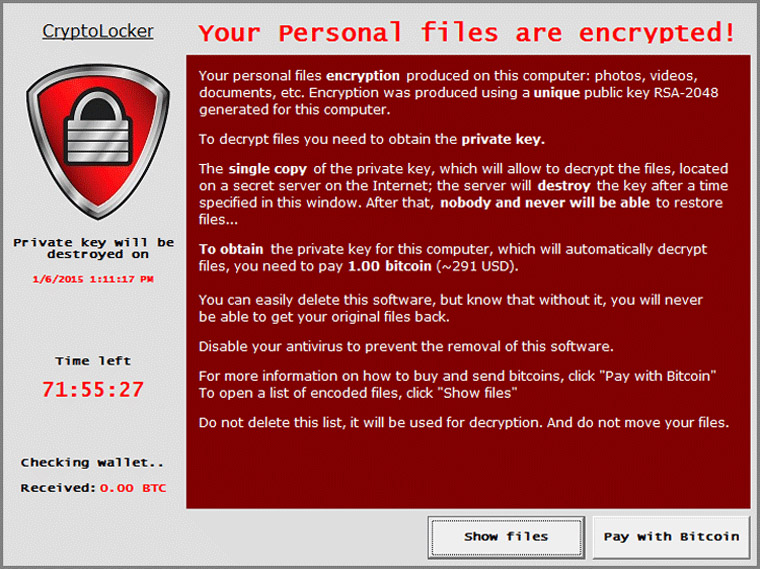
 CryptoLocker
Cryptolocker infected more than 250,000 systems.
Cryptolocker screenshot:
CryptoLocker
Cryptolocker infected more than 250,000 systems.
Cryptolocker screenshot:
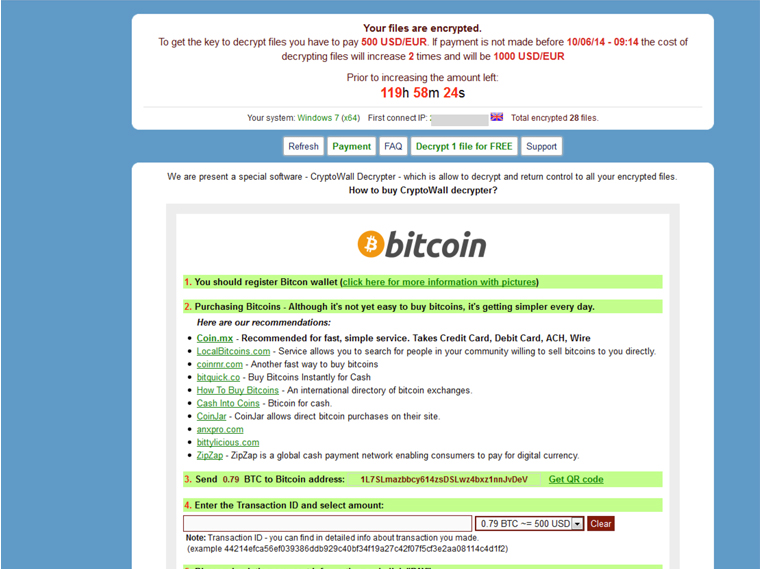
 CryptoWall
Has extorted over $18 million from victims. The FBI released an advisory.
CryptoWall screenshot:
CryptoWall
Has extorted over $18 million from victims. The FBI released an advisory.
CryptoWall screenshot:
 NotPetya
NotPetya far advanced its origins of Petya that’s why it’s called NotPetya.
NotPetya screenshot:
NotPetya
NotPetya far advanced its origins of Petya that’s why it’s called NotPetya.
NotPetya screenshot:
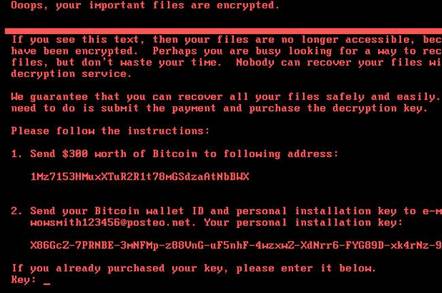 SamSam
Responsible for over $30 million in losses. First appearance in 2015 and is very common.
SamSam screenshot:
SamSam
Responsible for over $30 million in losses. First appearance in 2015 and is very common.
SamSam screenshot:
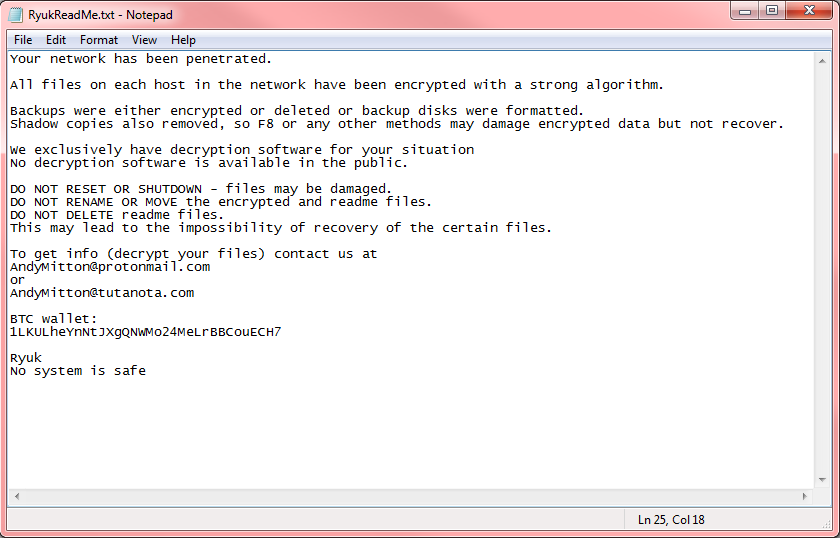
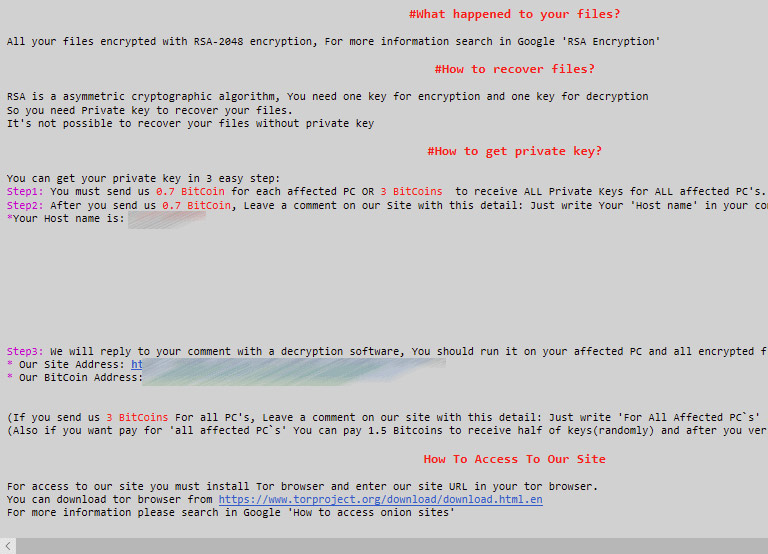 Ryuk
Popular in 2018 and 2019. Has the ability to disable Windows System Restore. Victims were targeted by large organizations.
Ryuk
Popular in 2018 and 2019. Has the ability to disable Windows System Restore. Victims were targeted by large organizations.

Anyone and any business can be a victim of ransomware. As long as you’re connected to a Wi-Fi or network, you’re a target.

Yes. There’s now more than 50 families of this malware in circulation! Cybercriminals know that there are people willing to pay to unlock their data, especially when it’s sensitive data or vital for business continuity.

July 25, 2019: City Power, the electric utility for Johannesburg, South Africa, discloses ransomware attack.
June 26, 2019: Lake City, Florida agrees to pay ransomware. June 20, 2019: Riviera Beach, Florida, discloses ransomware attack and payment. May 7, 2019: City of Baltimore hit with ransomware attack. April 2019: Cleveland Hopkins International Airport suffered a ransomware attack. April 2019: Augusta, Maine, suffered a highly targeted malware attack that froze the city’s entire network and forced the city center to close. April 2019: Hackers stole roughly $498,000 from the city of Tallahassee. March 2019: Albany, New York, suffered a ransomware attack. March 2019: Jackson County, Georgia officials paid cybercriminals $400,000 after a cyberattack shut down the county’s computer systems. Ransomware is more frequently seen in news stories than ever! Atlanta recovery cost $17 million after being hit with SamSam ransomware – ScMagazine.com. The original ransom demand was $51,000 in bitcoin but the recovery costs were over $17 million. Ransomware attacks on businesses are skyrocketing – Up 363% PCMag.com That’s a year over year increase on ransomware attacks businesses. The good news, attacks on consumers are down. Ransomware attacks: Weak passwords are now your biggest risk – zdnet.com Researchers say brute force and remote desktop attacks have become the mot common method for cyber criminals to spread ransomware. These cyber criminals are relying on weak and default passwords to easily gain access. They usually gain help from bots that will input as many passwords as possible. 2018 – 2019 ransomware stats 2 Iranians behind SamSam ransomware attacks, US claims – PCmag.com The 2 Iranian men were charged with computer hacking crimes that allegedly caused more than $300 million in losses and more than 200 known victims. Victims include: the city of Atlanta, the city of Newark, Port of San Diego, 6 health-care related groups, including LabCorp.

There are many free ransomware decryption tools. Check out the Crypto Sheriff at nomoreransom.org

The first step in preventing ransomware is knowing which types exist. They can be serious or easy to remove with a quick security scan. Here’s the three types of ransomware: Scareware, Screen Lockers, and Encrypting Ransomware.

Scareware:
This only mimics what real ransomware looks like. Your files are actually safe. You can remove scareware with a quick scan of your security software. Scareware usually consists of a popup window claiming there is a serious malware on your computer and you need to pay (a fake Microsoft agent) (etc.) to have it removed. There’s also a “1-800 number” listed on the popup. These numbers usually lead to an Indian scammer. Unsavvy computer users and the elderly are usually their number 1 targets. They are tricked into giving them remote access and paying hundres of dollars for “Microsoft support.”
Here’s an example of scareware: 
Screen Lockers freeze your screen, completely. There’s a few variations, usually claiming to be from the FBI or U.S. Department of Justice. There will be a claim that you were conducting some sort of illegal activity and you’ve been caught “red handed.” There is a request for you to pay a fine. You are likely to regain access to your computer by running a system restore or running a scan from a bootable CD or USB stick. Here’s an example of a Ransomware screen locker:


Encrypting ransomware is the result of a malware gaining access to your computer. Cyber criminals demand payment to unlock your files from encryption. Even if you pay the ransom, there’s no guarantee the cyber criminal will unlock your files. Unless you have a working backup of your files or a working decryption key, your files are gone.
Here’s an example of encryption ransomware: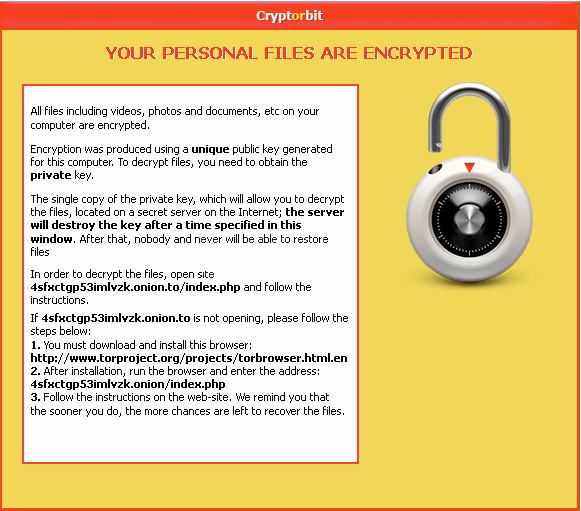

1. If you have a firewall, your data is 100% protected from ransomware. False. Cyber criminals can breach your database a variety of ways. A phishing attach can go undetected by your firewall. Since the threat landscape is always evolving, new advanced attacks need layers of security.
2. Only big companies are targeted by cyber criminals. False. Cyber criminals actually see small businesses as an easy pay day since budgets for security are usually small if there’s any security applied in the first place. Since 2011, we’ve seen a dramatic increase of cyber attacks targeting small business. 3. Data backups is all you need to recover stolen data. False. Not all backups are equal, not are they tested regularly. If a business is hit with ransomware, they need make sure their data backups were not also affected. In some cases, the cyber criminals will replace your data backups with replaced data.
Every 14 seconds in 2019, an organization is hit with a ransomware attack.

Yes. Android cell phones are a new popular choice for cyber criminals. Here’s a screenshot of ransomware on an android phone:
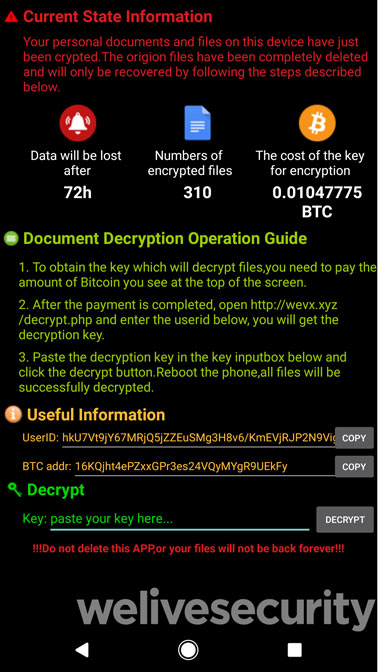

Rasnsomware can easily get on your phone if you download malicious apps. Fake apps from third party app store, porn apps, clicking on a spam link sent by SMS or from other forms of social engineering. An example of social engineering: You receive a DM in twitter from someone: “hey I found this pic of you online…LOL!”

One tip: Reboot your phone in Safe Mode and uninstall the app. Here’s how to reboot your android in Safe Mode: Hold your power button > Select “Power Off” > Turn on your phone by pressing and holding the Power button and Volume Up and Volume down buttons at the same time. Check for the words “Safe Mode” to appear on your screen. > Go to Settings > Applications > Manage Applications > Select the app you want to install. Didn’t work?
There’s other ways to start in safe mode, check with your phone’s manufacturer. Or just do a factory reset. All data will be wiped if you do a factory reset.
Cyber criminals prefer bitcoin because it’s fast, reliable, hard to trace, and verifiable. The cyber criminal will immediately be notified when you make a payment. Although bitcoin is the most popular, we’re seeing a new trend of Monero being used. It stops transactions from being traced!

$1 million was paid to cyber criminals from a South Korean web host. The payment was made to free their servers. 153 of their Linus server were attacked, hosting 3,400 websites. The ransom took place June 10, 2017. $162 million was the original ransom demand, however the price was negotiated down to $1 million.

Here’s the current most popular types of ransomware: Bad Rabbit, Cerber, CryptoLocker, CryptoWall, Crysis, CTB-Locker, GoldenEye, Jigsaw, KeRanger, LeChiffere, LockerGogo, Locky, NetPetya, Petya, Spider, TeslaCrypt, TorrentLocker, WannaCry, ZCryptor, and more. See all their screenshots here: Largest collection of ransomware screenshots to see more variations.

1. U.S.A, 2. Canada, 3. United Kingdom, 4. Brazil, 5. Italy

– “Your personal files are encrypting…” – “Your computer has been locked” – “FBI Online Agent has blocked your computer for a security reason” – “You became victim of the ______ RANSOMWARE!” – “WARNING! Your personal files are encrypted” – “YOUR FILE HAS BEEN LOCKED” – “All your files have been encrypted”

– A splash screen alerting you that your files are encrypted / or sometimes it’s a plain notepad of instructions – Inform you that you need a decryption key Instructions how to obtain a key – The cost of a private key to unlock your files (The cost is most commonly shown in bitcoins) – Time limit – The bitcoin address to send your payment Sometimes a help section is included Sometimes they want you to download the TOR browser (dark web) – A place to submit your key with unlock button Sometimes they inform you the price will go up

If you have an of the following signs, you’re an easy target for ransomware:
#1 Outdated Equipment Old computers are a security risk. The newer the technology, the more security. The more up to date your hardware, the more difficult it is for cyber criminals to get your data. #2 Your Browser and Operating Systems are Unpatched 25% of the world’s desktop computers are still running Windows XP. Because this operating system is no longer receiving patches or or security updates – the risk of getting hacked increase every day, #3 You’re using Legacy Software Legacy software implies that the system is old and out of date. The older the version of software, the more patches and updates it needs and hackers know all the vulnerabilities. The cost of running legacy is actually greater than upgrading. #4 You don’t have a cyber security strategy in place Many small businesses are actually an easier target to cyber criminal because they don’t have a cyber security strategy in place. They may not have an IT person on staff or outsourced IT department. This not only puts their company at risk, but also their customers information. Without cyber security in place, your company is a sitting duck. Sadly, if your business gets hit with ransomware and you lose all your data – only 6% of companies survive longer than two years after losing data. #5 You don’t have a working backup plan Ransomware puts all your data at risk, can you afford to lose it? You need a data backup for a few reasons, in case a natural disaster strikes, human error, ransomware, etc. Without a working data backup, your company is vulnerable to having to “pay the ransom.” Worst, you might pay the ransom and you don’t get the key to decrypt your files. #6 Your employees open and download attachments Believe it or not, the biggest risk your business faces against ransomware is your employees. They’re prone to human error, accidentally opening emails that have ransomware attached. #7 Your employess’ mobile devices are connected to the network
– Downtime is more costly. The average ransomware attack on the business costs 10 times more than the actual ransom. The survey finds the costs on average, $46,800, and the ransomware request at $4,300 per attack.
– Attacks are expected to increase. More than 55% of MSPs (managed service providers) disclosed their customers experienced a ransomware attack within the first 6 months of 2018. 35% said their customers were attacked multiple times in the same day. 92% of MSPs predict ransomware attacks will continue at or increase in rates. – Antivirus software is not enough, they’re actually ineffective. 85% of MSPs reported that victims of ransomware already had antivirus installed. 65% said victims had email spam filters installed. 29% reported that victims had pop-up blockers that failed to block the ransomware attacks. – Apple operating systems can be vulnerable to ransomware. There was a 5X increase in the number of reported ransomware attacks on macOS and iOS platforms. – Less than 1 in 4 ransomware attacks are reported to authorities The problem may be actually bigger than we even know. – New Ransomware strains include Public Shaming. Some versions of ransomware claim to have taken photos of you from your web camera. They also claim to blackmail you deeming the photos were taken of you viewing pornography, and threaten to publish them. Perhaps send them to everyone on your contact list.The FBI and Law Enforcement cannot help you. – The FBI will usually recommend that you pay the cyber criminals to gain back access to your computer. – The average ransomware payment is around $300.00. Individuals are the most common victim of ransomware. And the forms of payment preferred are Bitcoin or green dot MoneyPak. Both untraceable. – The ransomware Cryptowall 3.0 has profited over $325 million. Cryptowall emerged in January 2015 and experts estimate the group cause $325 million in damages across the world, primarily from the US. – Adobe Flash is to blame for recent Ransomware spread. 8 of the top 10 vulnerabilities were discovered to be Flash-related. – Malvertising Fuels Ransomware. Phishing is a huge cause of ransomware, and now malvertising is becoming popular too. Many news sites had their advertisements hijacked with ransomware. – Cyber Criminals can Buy Ransomware-as-a-service (SaaS) model. Cyber criminals are shopping the black market for ransomware-as-a-service, giving the developers a share of their earnings. – Ransomware is also hitting Linux and OSX, mobile devices such as smartphones. – Anti-Virus software isn’t enough. With new variants of malware evolving everyday, traditional signature-based anti-virus products can’t keep up. – Ransomware can disguise themselves as porn apps. – The United States has the most ransomware detection’s: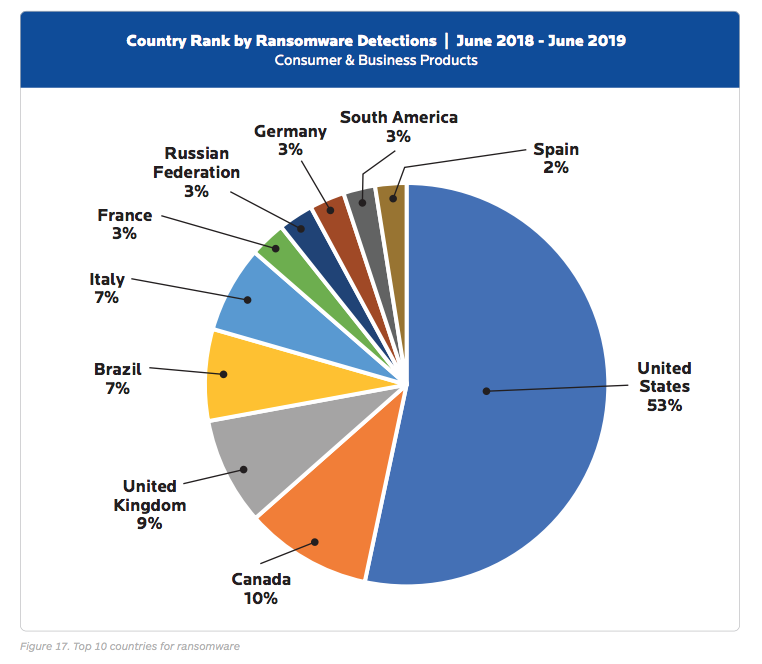
If you already failed to avoid ransomware it’s probably too late. Unless you run you malware and anti-virus scanner frequently with updated definitions, your software will alert you. You can possibly quarantine and remove the ransomware.

Ransomware Survival Checklist Before | During | After
The BAD news, ransomware isn’t going away, in fact, it’s here to stay. The GOOD news, the sooner you realize this statement “my business is too small to get hit with ransomware” is not feasible, the better! Yay! Why is ransomware flourishing? Simply because most companies are NOT prepared for a ransomware threat. Ponemon Institute’s 2016 State of Endpoint Report reveals 56% of companies are not ready to fight off ransomware attacks.Tantalizing news for cyber criminals right?If you use this ransomware survival guide checklist, your small business will defiantly be “beefed up” to ransomware.
BEFORE: Preventing Ransomware
- Invest in a robust data backup and restore solution + testing backups – The most important golden step to preventing ransomware affecting your business
- Update and patch – Many businesses struggle keeping up-to-date, making them vulnerable
- Train and educate your employees about phishing emails, social engineering, macros, and ransomware
- Invest in email filtering – Most ransomware is transmitted by email
DURING: Getting Back to Business
- Call the FBI – Ransomware is a crime–theft and extortion are in play
- Disconnect from your network – take the infected machine to the IT department
- Determine the extent of the problem – Who in the network is compromised? What type of ransomware?
- Pay or Play? – We recommend you don’t pay a ransom and restore from backups
- Don’t count on free ransomware decryption tools – Free tools quickly become outdated
- Restore from backup – You should be backing up everyday
AFTER: Review and Reinforce
- Clean up – Wipe your devices and restore from a clean backup
- Examine – How can we improve network configurations?
- Assess your employee awareness – Address employee vulnerability
- Invest in modern defenses – Hackers are usually one step ahead of you
- Invest in managed IT services – Don’t rely on one employee for your cyber security needs



